
Deep packet inspection (DPI) is an advanced method of analyzing traffic being sent over a network. DPI uses data processing to inspect specific details of packets as a form of packet filtering.
While DPI is used to look at layer 2-7 of the OSI model, a device is only considered DPI-enabled if it can look at and take action based on layer 3 or higher.
By examining the unique features of a packet such as headers, protocol fields, payloads, and other data, DPI can identify, redirect, prioritize, or even block packets that meet certain criteria.
Because deep packet inspection is able to determine the content of messages, it can identify the specific application or service a message originated from.
As packets pass through a given checkpoint, DPI helps make real-time routing decisions based on policies designated by a network manager, organization, or internet service provider (ISP). This is beneficial for both network traffic management and network security.
DPI can be used to streamline the flow of traffic on a network to improve the network’s performance. For example, if business-critical packets are tagged as high-priority, DPI can give them preference over those less crucial and ensure they are forwarded to their destination immediately. Additionally, DPI can throttle data transfers by identifying and prioritizing a particular transmission type.
Managers can also utilize DPI to control which applications workers have access to. By setting filters to detect or reroute network traffic from a specific IP address range, or certain online services, DPI can block unauthorized applications that violate company policy or hinder productivity.
DPI is also an important component of network security because it helps detect threats and intrusions at the network layer. By searching for and intercepting malicious traffic, spam, and protocol non-compliance, DPI can prevent malware and viruses from spreading through the entire network.
For example, DPI is often included in firewalls to identify and block packets from specific IPs to protect against buffer overflow, DDoS attacks, and a wide range of other threats. Unfortunately, adding DPI to firewall appliances can often lead to performance degradation causing network bottlenecks and increased latency.
Many network service providers (NSP) and operators are required to have a DPI engine so they can supply internet communications to law enforcement if a warrant is served. Using a DPI-enabled device the service provider can identify traffic from a specific subscriber and provide law enforcement with either just the signaling information or the specific content of the application.
OTT platforms such as Netflix and Amazon Prime, often partner with NSPs to ensure their traffic is getting priority on the network. By implementing DPI, NSPs can deliver accurate accounts of how many users are watching as well as how much priority was given to which traffic so they can easily calculate any revenue sharing.
DPI can also be used to mitigate DDoS attacks. When people leave default usernames and passwords on devices like CCTVs and Wi-Fi routers, they become easy hacking targets. By converting thousands of these devices to automated bots, attackers can flood a website with thousands of requests at once. DPI can identify spikes like this going to a specific destination and trigger DDoS mitigation.
Since DPI plays an essential role in network traffic management and network security, testing DPI functionality is crucial. Traffic generators are especially important in validating the DPI capabilities of a device for accuracy and performance. By analyzing metrics like throughput and packet loss while sending various frame sizes of good and malicious traffic, traffic generators can help you optimize the performance of DPI-enabled devices.
There are two schools of testing DPI with a traffic generator. You can capture real traffic on your network, and amplify it to a very high scale to measure the maximum load your DPI-enabled device can successfully manage. Or alternatively, choose a traffic generator with a library of application flows, and select a variety of traffic to send through your device to determine if the DPI is blocking the malicious traffic and giving the correct prioritization to other applications.
The diagram below shows an example of a test setup for a DPI-enabled firewall.
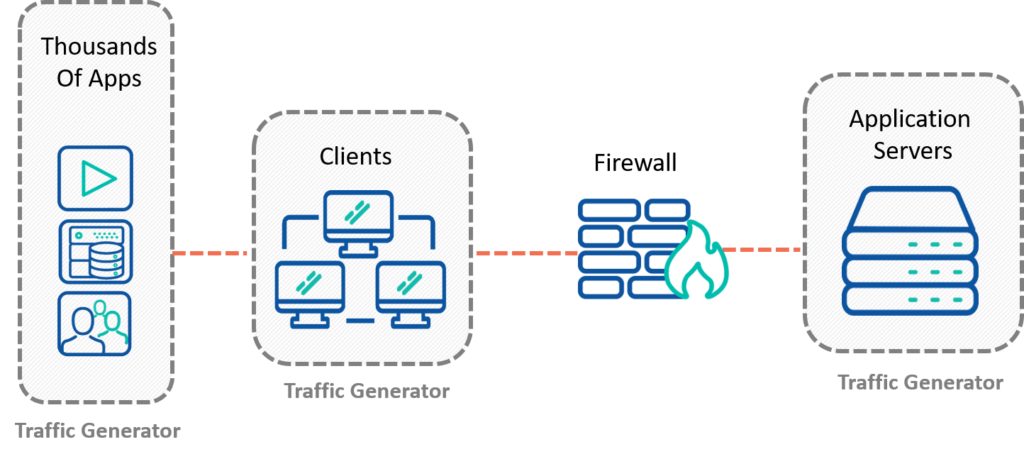
If you have further questions about testing DPI-capable devices, please reach out to us at contact us.